Table of Contents
Executive Summary
The rise of AI agents, code generation, and so-called “vibe-coding” is forcing investors to fundamentally reassess what constitutes durable software IP. Large parts of traditional enterprise software — particularly workflow-driven, UI-heavy, seat-based SaaS — face real structural pressure as AI lowers development costs, reduces switching frictions, and compresses pricing power.
Cybersecurity, however, represents a clear exception.
While cybersecurity stocks have sold off alongside broader software amid concerns around AI-driven commoditization, budget scrutiny, and multiple compression, their underlying business fundamentals remain structurally intact — and, in some cases, improving. Unlike generic enterprise software, cybersecurity platforms are built around adversarial intelligence, proprietary threat data, and continuously evolving detection logic that cannot be easily replicated by AI agents or internal development teams.
This creates a compelling relative-value opportunity: short broad enterprise software exposure (e.g., IGV) while going long a basket of best-in-class cybersecurity platforms such as Palo Alto Networks (PANW), CrowdStrike (CRWD),and Zscaler (ZS). The trade is designed to isolate dispersion within software rather than take outright market beta, positioning for cybersecurity to outperform as investors increasingly differentiate between replicable software and truly defensible platforms.
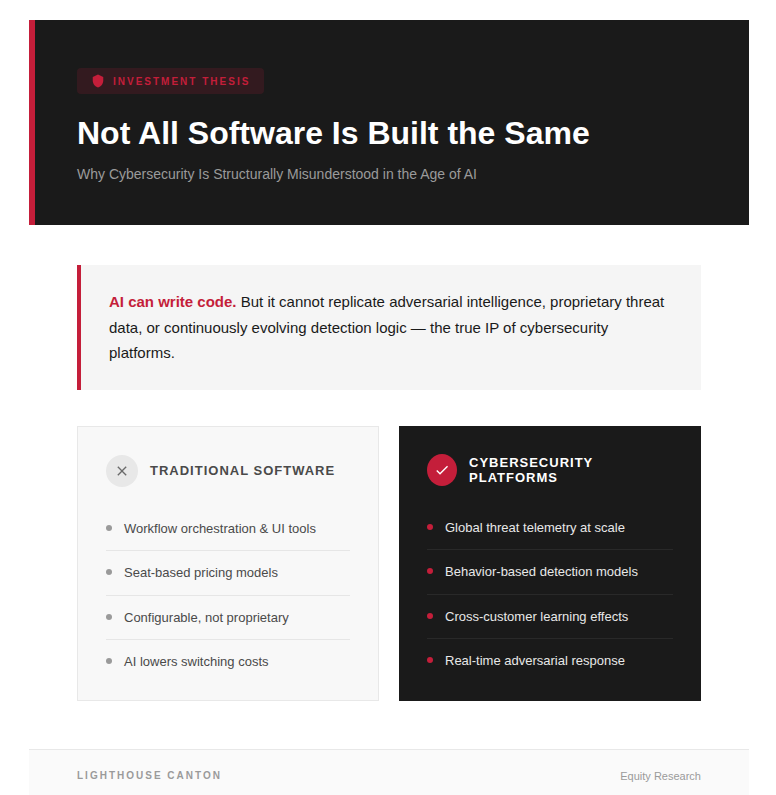
The Core Fallacy: Treating All Software as Replicable Code
A central assumption driving the current de-rating of software equities is simple: if AI can write code, then software moats must collapse.
This logic is directionally correct, but only for certain categories of software.
Much of enterprise software developed over the past decade is best described as:
- Workflow orchestration
- UI-driven productivity tooling
- Configurable systems rather than proprietary engines
- Economically tied to human headcount via seat-based pricing
In these segments, AI is a direct threat. Internal tools can be rebuilt faster and cheaper. Custom workflows can be generated in-house. Switching costs decline as integrations become agent-driven rather than vendor-specific. The traditional “subscription per seat” model begins to look structurally fragile.
This is where cybersecurity diverges.
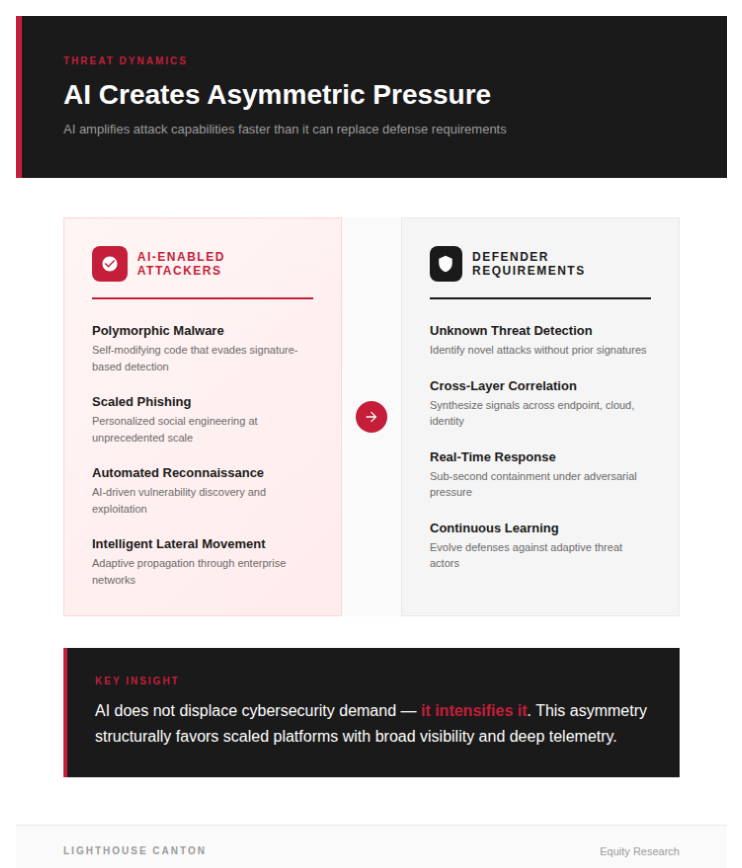
Why Cybersecurity Is Fundamentally Different
1. The IP Is the Intelligence, Not the Interface
In cybersecurity, the UI is largely incidental. The real intellectual property resides in:
- Global threat telemetry across millions of endpoints and workloads
- Behavior-based detection models refined through live attacks
- Cross-customer learning effects and feedback loops
- Real-time response orchestration under adversarial conditions
These are not assets that can be recreated through prompt engineering or lightweight code generation. Cybersecurity platforms compound their advantage over time as data scale increases and threat models mature.
2. AI Expands the Threat Surface Faster Than It Replaces Defense
AI acts as a force multiplier for attackers:
- Malware becomes polymorphic and adaptive
- Phishing and social engineering scale and personalize
- Reconnaissance and lateral movement become automated
Defenders, by contrast, must detect unknown threats, correlate signals across endpoints, cloud, identity, and network layers, and respond in real time. This asymmetry structurally favors scaled cybersecurity platforms with broad visibility and deep telemetry.
AI does not displace cybersecurity demand — it intensifies it.
3. Cybersecurity Is Not Fundamentally a Seat-Based Business
Traditional enterprise software demand scales with employee count. Cybersecurity demand scales with exposure:
- Endpoints
- Cloud workloads
- Identities
- APIs
- Network traffic
As enterprises become more automated and AI-driven, system complexity and attack surface expand even if human headcount does not. This dynamic underpins the long-term resilience of cybersecurity spend relative to other software categories.
4. Replacement Risk Is Low; Consolidation Risk Is High
Where enterprise software faces replacement risk, cybersecurity faces consolidation risk — a far more favorable dynamic. CISOs increasingly prefer fewer vendors, broader platforms, and proven efficacy. As a result, category leaders gainshare while weaker point solutions are displaced.
This structural trend benefits scaled platforms such as PANW, CRWD, and ZS, rather than undermining them.
Why Cybersecurity Stocks Still Sell Off
Despite these fundamentals, cybersecurity equities are often treated as indistinguishable from the broader software complex. The sell-offs are driven by:
- Indiscriminate de-risking via software ETFs
- Multiple compression across long-duration growth assets
- Short-term budget optimization fears
These pressures are largely optical rather than structural, creating the risk that cybersecurity becomes collateral damage in a broader reassessment of enterprise software economics.

The Trade: Expressing Dispersion Within Software
Rather than taking a binary view on software, the opportunity lies in exploiting internal dispersion:
- Short: Broad enterprise software exposure (e.g., IGV), where AI poses genuine structural challenges to business models
- Long: A basket of best-in-class cybersecurity platforms (PANW, CRWD, ZS), where AI acts as a demand accelerant rather than a disruptor
This structure hedges duration and multiple risk while isolating exposure to software businesses with durable, non-replicable IP.
Bottom Line
AI is forcing a necessary reckoning across enterprise software. But in the process, the market risks flattening critical distinctions between replicable workflows and adversarial intelligence platforms.
Cybersecurity does not lose relevance in an AI-driven world. It becomes more essential.
The mispricing lies not in software broadly — but in failing to recognize that not all software is built the same.














%20(29).jpg)
%20(27).jpg)
.jpg)
.png)